
In today's digital age, safeguarding your data is paramount. Simply creating a copy of your files may not be enough as they can get corrupted, overwritten or blocked by ransomware. Having multiple, time-rotated (and ideally, offsite) backups is a stronger defense. I created a new tool, rsync-backup-rotator, to help you with this.
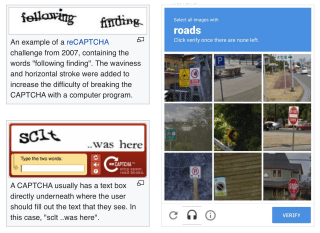
Chances are that you've encountered a CAPTCHA in the wild: they protect web forms by asking you to type over weirdly rendered characters or by asking you to select photos containing a particular thing. Why are they used and is there a user friendly alternative?

Nearly all folks I know use iOS or Android from a mainstream smartphone brand, yet alternatives still exist! The German Volla Phone prides itself to be a worthy option for those who value privacy and freedom. I bought one to experience it firsthand, read along for my thoughts!
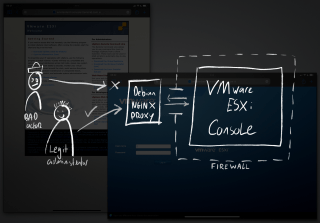
In response to an incident on a server, I detected a possible security breach. The affected machine ran VMware ESXi, a bare metal hypervisor used to run virtual private servers. In standalone mode, a web based management console offers full control over the infrastructure, posing a risk.
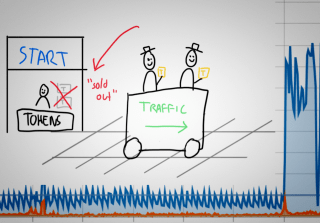
Last month I received an automated alert indicating excessive bandwidth usage, usually a sign of trouble. When this happens, you should follow a standard incident procedure, trying to isolate the source of the traffic before shutting it down. The cause of this incident was not what I expected however... requiring a different kind of mitigation than a simple blockade.

This month I was lucky enough to attend Global AppSec Amsterdam, an international conference for hackers and security specialists. There were presentations from former intelligence agents, bounty hunters, academics and software vendors. I learned about some of the newest hacking techniques, met with interesting people and played some cool retro games. Read along for more.
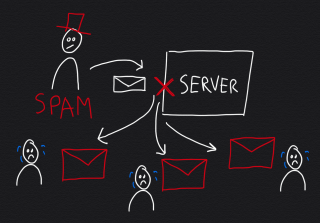
This month I had to deal with backscatter spam, affecting one of the mail servers I manage. As server engineer I make sure that servers don't send spam and that incoming email gets filtered. Despite all good efforts, this server kept being blacklisted for sending spam to iCloud, Office 365 and Google Gmail for Business (G Suite). Read along to find out how what caused this and how to fix this.

When you're building websites, apps or email services you may run into domain names and their configurations. When everything is working as it should, most of this is invisible. But when troubleshooting a domain name configuration, it may be necessary to dig a little deeper... read along to learn how!

You probably use the world's most famous search engine to find things everyday, but you might not know about some of its advanced search operators. You can use these special search phrases to find things that are otherwise burried in the search results. Read along for a comprehensive list of advanced Google search operators.

A lot of people use WordPress to manage their website, therefore it's no surprise people ask me to have a look at their site's security. As ethical hacker, I encounter WordPress in different shapes, sizes and states. Some of them are really badly protected against hacks. Prevent your site from being hacked using these 10 practical tips.

People pay me to hack them, provided I'll explain how it was done, so future hacks can be prevented. As security consultant, I scan for weaknesses in my clients' apps, webshops and websites. Very often a hack starts by exploiting a security hole that is visible remotely. Read along to learn how hackers find security holes and what you can do to secure them.

This week one of my clients was hacked and asked me for emergency assistance to help secure their server infrastructure. It was a web server that ran WordPress websites on Apache (with PHP/MySQL), including a few webshops with customer data. This hack could easily have been prevented with the following best practices, is your server secure?