














In today's digital age, safeguarding your data is paramount. Simply creating a copy of your files may not be enough as they can get corrupted, overwritten or blocked by ransomware. Having multiple, time-rotated (and ideally, offsite) backups is a stronger defense. I created a new tool, rsync-backup-rotator, to help you with this.
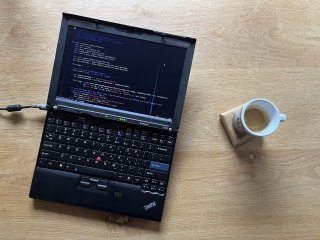
As part of a greater plan to optimise my entire workflow, I am doing a little experiment this month: using a 15-year old ThinkPad X200 laptop as main computer. It’s from an era before “the cloud”, popular among free/libre software enthusiasts. What can we learn from this antithesis of modernity?

Like many, I faced soaring cloud service costs for my clients, prompting a wake-up call. To stay afloat, it's essential to incorporate software optimisation as a strategy for managing cloud expenses. Join me as I share how I managed to save up to 90% on cloud costs through optimisation!
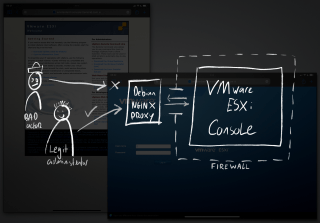
In response to an incident on a server, I detected a possible security breach. The affected machine ran VMware ESXi, a bare metal hypervisor used to run virtual private servers. In standalone mode, a web based management console offers full control over the infrastructure, posing a risk.

For a Dutch organisation that serves customers throughout Europe, I was asked to help dismantle a live server room. Instead of simply pulling the plugs, some of the services had to be migrated to the cloud. For fun and inspiration I share three different strategies to do so.

The past year I have been experimenting with creating my own tablet operating system using Debian GNU/Linux and the i3 window manager on a Microsoft Surface Go 2 with LTE. After months of intense use I have now decided to abandon the experiment to move back to iPad Pro and the Mac. Read along to find out why.
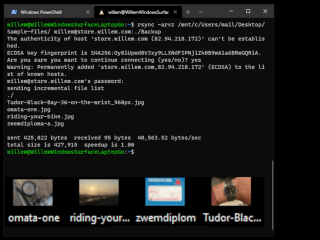
It is very important to make backups of your data, as you never know when disaster strikes! One powerful, cross platform, tool to help you achieve this is 'rsync'. In this post I'll explain why rsync is useful and how you can use it to set up your own backups.

Earlier this year I tried to create my own tablet operating system by installing Debian GNU/Linux on a Microsoft Surface Go tablet. I learned a great deal about what I like about tablets. But I still preferred my iPad Pro, mainly because of its polished user experience. This time I set out to refine my tablet software to replace my iPad.

In order to optimise my workflow, I was looking for a way to seamlessly access the same files on both my computer and smartphone. This is useful to when you want to quickly send files from your computer using your smartphone through various messaging apps and vice versa. Read along to find out how I did it.

After encountering the umpteenth ‘magic’ bug while managing my iPhone’s photos, I was done with it. Apple came a long way since it launched iPhoto (the predecessor of iCloud Photos). But for something as valuable as my personal memories, I want to be in full control. Read along to learn how I migrated my photo library away from the iCloud, using free, open source software.
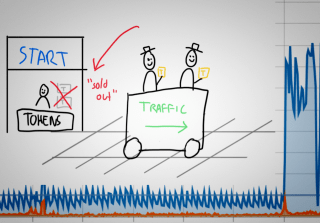
Last month I received an automated alert indicating excessive bandwidth usage, usually a sign of trouble. When this happens, you should follow a standard incident procedure, trying to isolate the source of the traffic before shutting it down. The cause of this incident was not what I expected however... requiring a different kind of mitigation than a simple blockade.

For some years now I use a tablet as main computer, I like its versatility. But, most tablets come with a locked down operating system, like iPadOS, Windows 10S or Android. As I like things my own (weird) way, I wondered if I could escape these "software jails" by installing a free operating system on a tablet. It's possible, read along to find out how I escaped!
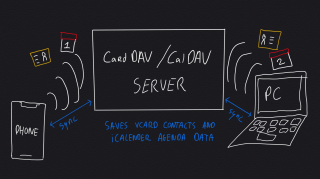
If you use different devices and computers to get things done, you might want to synchronise contacts, agendas and tasks. You can use any of the 'big cloud' services for this, like Apple iCloud, Microsoft Office 365 and Google Gmail. But, if you prefer not to share your addressbook and calendar with big American companies, you can do it yourself.

Over the past few years I have been moving my data and work from local computers (mostly laptops) into the cloud. Cloud computing is done by servers in a datacenter, powerful computers that do the hard work. As my company grew, I needed more capacity. It was time to add some power to my cloud!
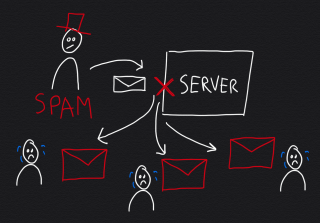
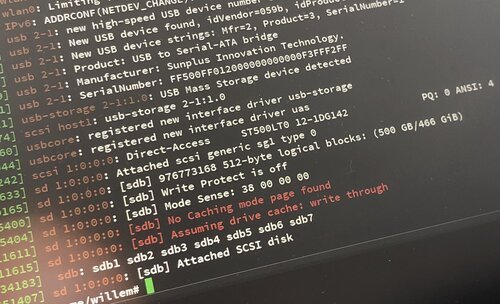
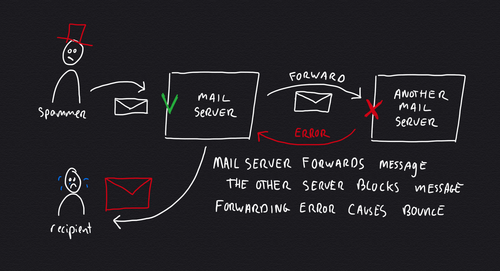
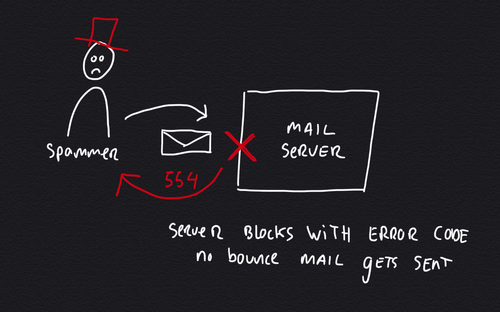
This month I had to deal with backscatter spam, affecting one of the mail servers I manage. As server engineer I make sure that servers don't send spam and that incoming email gets filtered. Despite all good efforts, this server kept being blacklisted for sending spam to iCloud, Office 365 and Google Gmail for Business (G Suite). Read along to find out how what caused this and how to fix this.

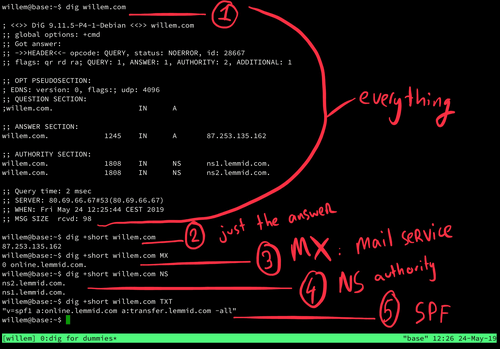
When you're building websites, apps or email services you may run into domain names and their configurations. When everything is working as it should, most of this is invisible. But when troubleshooting a domain name configuration, it may be necessary to dig a little deeper... read along to learn how!

People pay me to hack them, provided I'll explain how it was done, so future hacks can be prevented. As security consultant, I scan for weaknesses in my clients' apps, webshops and websites. Very often a hack starts by exploiting a security hole that is visible remotely. Read along to learn how hackers find security holes and what you can do to secure them.

This week I went to Frankfurt for business. I had to perform maintenance to servers in a data centre. This seemed like a great opportunity to test the Apple Watch's usefulness in real life (other than health and fitness). I wondered, is the Apple Watch the modern tool watch?

Yesterday a young woman brought me her laptop, it didn't start anymore and it only showed an error message. It turned out to be a broken harddisk. It startled her when I told her that all data on the disk was lost. She told me it contained precious photos of her pregnancy and young child. What could I do?
This month I have been working on website statistics, tracking traffic using different technologies. Some of my customers use Google Analytics, others use AWStats, and some use both. Which is better is often debated, but few people really understand the differences. Time to shed some light on the magic of web statistics.

This week a man brought his laptop to the community centre where I help people with computer problems as volunteer. The old laptop wouldn't start anymore and had to be reinstalled. Instead of Windows, I installed a free operating system. I think it is important to tell you how and why I did it.

This week one of my clients was hacked and asked me for emergency assistance to help secure their server infrastructure. It was a web server that ran WordPress websites on Apache (with PHP/MySQL), including a few webshops with customer data. This hack could easily have been prevented with the following best practices, is your server secure?

For the past few weeks I have been using the Microsoft Surface Pro as my main computer. It's a modern tablet computer that can be used as laptop with the type cover. With the Surface Pen, it's a versatile PC that works in a lot of different ways. Time to find out if it's any good and how it compares to my other tablet computer, iPad Pro.

About five months ago I got some take away food from our local Asian restaurant. They packaged the food and gave me a plastic bag to carry it home. On my way home I was thinking about the bag. Although it has some nice styling printed on it, it's designed for single use only. What a waste... making me wonder: how long would it last if you would use it on a daily basis?

At my home I have this crazy fast optical internet connection. It is a 600MB up and down fibre connection which directly arrives in my home (no copper cables involved). It's like a private internet highway. Reason enough to find out if I could do something to make better use of all this speedy fiber galore...

Today I called my provider to quit my office's ADSL internet subscription, I don't need it anymore. I have turned off my local area network and switched my workflow onto mobile internet only. The simplicity and savings actually surprised me so much, that I made blog post for it.

Over the past years I have been no stranger to crazy experiments, but this time I really wanted to push it into the extreme: programming on an Apple Watch. Would it be possible to actually write code on such a tiny device? Why even bother? This post is about the case for crazy experiments, and why you should try too!

The lack of physical clutter, distracting branding, or blinking LED's makes the iPad Pro a textbook example of minimal design. My despiction of distraction explains my interest in using the iPad Pro as only computer to test if it is up to the task. Is Apple's latest effort on iOS enough to enable it to do serious development work?

One must be a bit crazy to come up with the idea to build a blog (as in: actual programming) on an old 486 laptop with just 16MB RAM. I happen to be that crazy: I took my very first laptop from the 90s and decided to find out if it was possible to turn it into a development machine.

















