

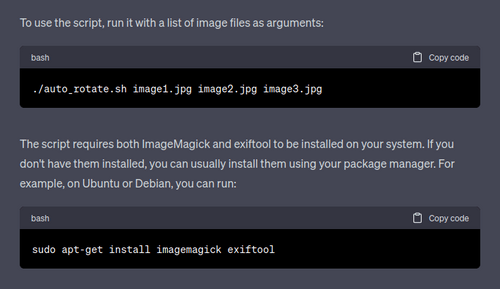





In today's digital age, safeguarding your data is paramount. Simply creating a copy of your files may not be enough as they can get corrupted, overwritten or blocked by ransomware. Having multiple, time-rotated (and ideally, offsite) backups is a stronger defense. I created a new tool, rsync-backup-rotator, to help you with this.

As part of my software optimisation efforts to cut cloud costs, I needed to replace an existing piece of inefficient server software with something that uses more robust (yet fragmented) tooling available in Debian GNU/Linux. Could the GPT4 language model deliver me some AI magic? Read along!

Like many, I faced soaring cloud service costs for my clients, prompting a wake-up call. To stay afloat, it's essential to incorporate software optimisation as a strategy for managing cloud expenses. Join me as I share how I managed to save up to 90% on cloud costs through optimisation!
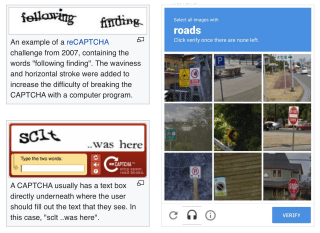
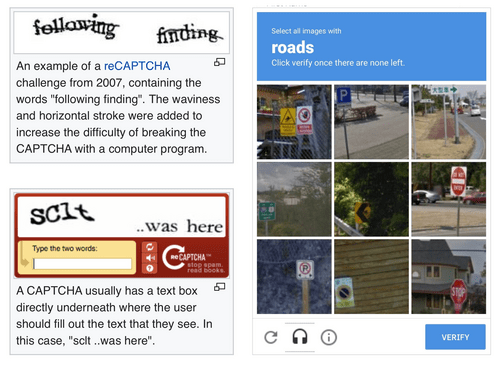
Chances are that you've encountered a CAPTCHA in the wild: they protect web forms by asking you to type over weirdly rendered characters or by asking you to select photos containing a particular thing. Why are they used and is there a user friendly alternative?
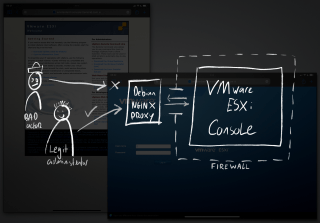
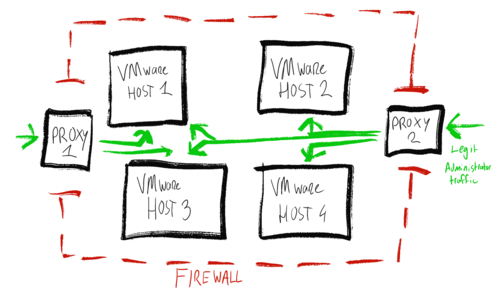
In response to an incident on a server, I detected a possible security breach. The affected machine ran VMware ESXi, a bare metal hypervisor used to run virtual private servers. In standalone mode, a web based management console offers full control over the infrastructure, posing a risk.

For a Dutch organisation that serves customers throughout Europe, I was asked to help dismantle a live server room. Instead of simply pulling the plugs, some of the services had to be migrated to the cloud. For fun and inspiration I share three different strategies to do so.

Downtime happens and it is nothing to be ashamed of, just make sure that you set yourself up to discover problems as soon as possible! You can use realtime uptime monitoring to automatically keep an eye on your servers and services. Read along to find out how.
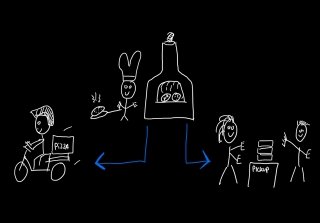
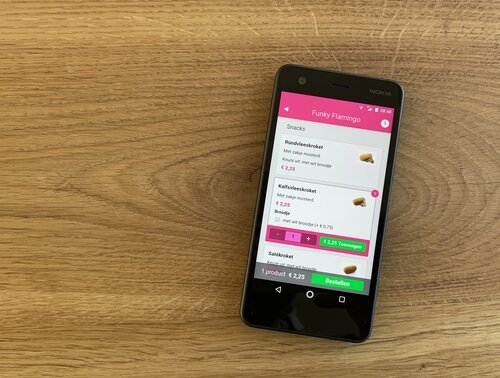
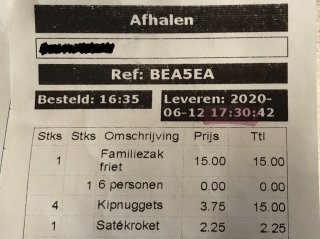
This month I needed to create additional dimensions to a capacity queue mechanism. The food ordering app that I created needed to be able to restrict capacity based on the number of orders, the contents in individual orders and the dispatch type (takeaway/delivery). Read along to find out how I used a Lambda Architecture to do this.
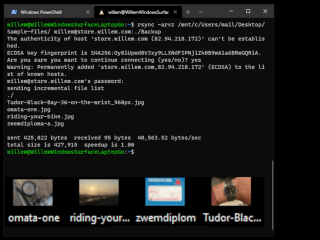
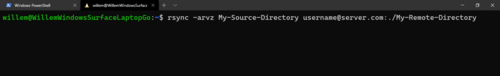
It is very important to make backups of your data, as you never know when disaster strikes! One powerful, cross platform, tool to help you achieve this is 'rsync'. In this post I'll explain why rsync is useful and how you can use it to set up your own backups.

In order to optimise my workflow, I was looking for a way to seamlessly access the same files on both my computer and smartphone. This is useful to when you want to quickly send files from your computer using your smartphone through various messaging apps and vice versa. Read along to find out how I did it.
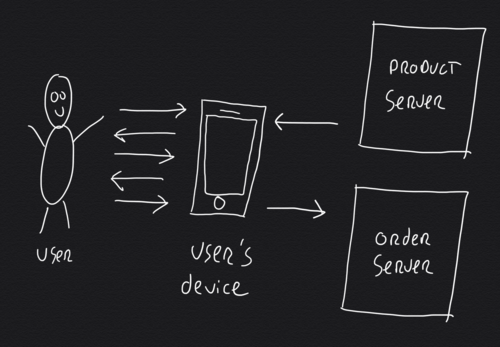
As part of the food ordering app I am building, I needed to design a reliable way to link the app to external systems. These external systems are beyond my direct control and include different checkout registers, kitchen management systems and ticket printers. Read along for more on designing for the unknown and unreliable.
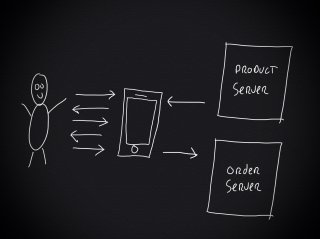
As part of the online food ordering app I'm building, I needed to design a scalable backend infrastructure that could handle lots of concurrent users. Scalability is considered a hard problem to tackle. Often it's presented like it's something magical, done by million dollar companies using secret tools. But, there is no such thing as magic, or is there?
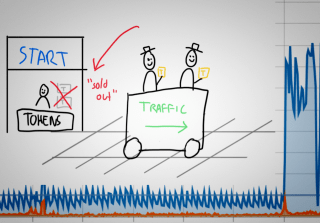
Last month I received an automated alert indicating excessive bandwidth usage, usually a sign of trouble. When this happens, you should follow a standard incident procedure, trying to isolate the source of the traffic before shutting it down. The cause of this incident was not what I expected however... requiring a different kind of mitigation than a simple blockade.
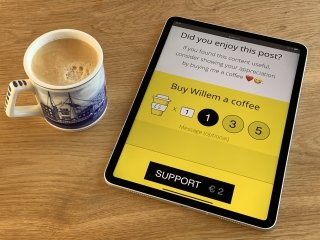
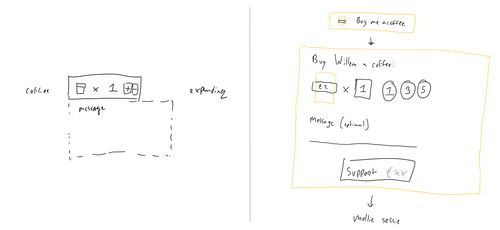
Online payments are now more important than ever as businesses are disrupted by the COVID-19 virus. It drives my customers to seek new ways to make money online. I designed and implemented a (micro)payment system. This post is about achieving simplicity by solving complex challenges.

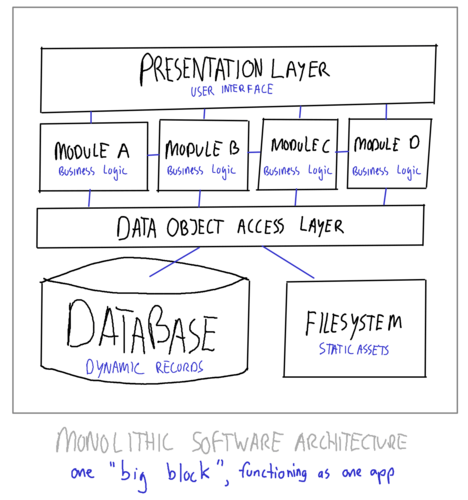
This week I flew to Gothenburg to meet people from a large international shipping company, talking about the development of enterprise level software. During the meeting there were various experts in the room, one of them asked me on choosing the right software architecture (for big, complex, enterprise level apps). A very good question, well worthy for a blog post.
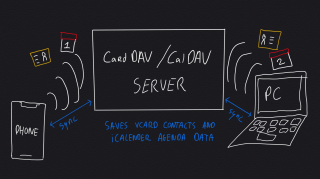
If you use different devices and computers to get things done, you might want to synchronise contacts, agendas and tasks. You can use any of the 'big cloud' services for this, like Apple iCloud, Microsoft Office 365 and Google Gmail. But, if you prefer not to share your addressbook and calendar with big American companies, you can do it yourself.

Over the past few years I have been moving my data and work from local computers (mostly laptops) into the cloud. Cloud computing is done by servers in a datacenter, powerful computers that do the hard work. As my company grew, I needed more capacity. It was time to add some power to my cloud!
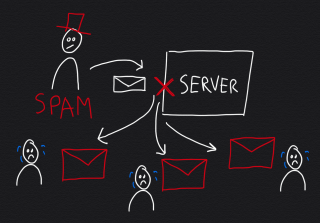
This month I had to deal with backscatter spam, affecting one of the mail servers I manage. As server engineer I make sure that servers don't send spam and that incoming email gets filtered. Despite all good efforts, this server kept being blacklisted for sending spam to iCloud, Office 365 and Google Gmail for Business (G Suite). Read along to find out how what caused this and how to fix this.

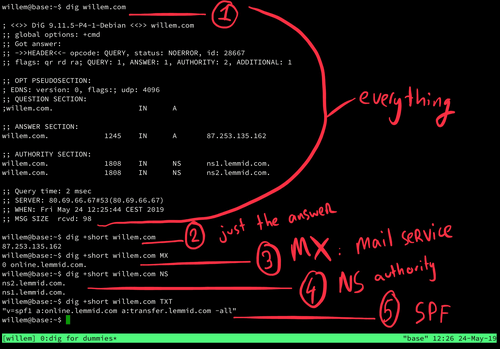
When you're building websites, apps or email services you may run into domain names and their configurations. When everything is working as it should, most of this is invisible. But when troubleshooting a domain name configuration, it may be necessary to dig a little deeper... read along to learn how!

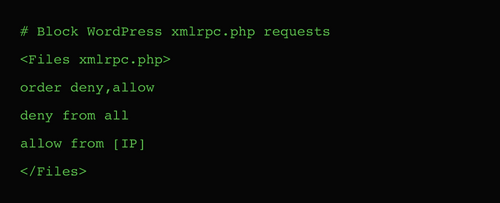
A lot of people use WordPress to manage their website, therefore it's no surprise people ask me to have a look at their site's security. As ethical hacker, I encounter WordPress in different shapes, sizes and states. Some of them are really badly protected against hacks. Prevent your site from being hacked using these 10 practical tips.

People pay me to hack them, provided I'll explain how it was done, so future hacks can be prevented. As security consultant, I scan for weaknesses in my clients' apps, webshops and websites. Very often a hack starts by exploiting a security hole that is visible remotely. Read along to learn how hackers find security holes and what you can do to secure them.

This week I went to Frankfurt for business. I had to perform maintenance to servers in a data centre. This seemed like a great opportunity to test the Apple Watch's usefulness in real life (other than health and fitness). I wondered, is the Apple Watch the modern tool watch?
One way to make your website faster is to make it smaller. Not with tiny fonts, but with less bytes! More than half the weight of an average website is because of images. Yet very few people optimise their images for the web and performance, time to find out how much bytes you can safe!
This month I have been working on website statistics, tracking traffic using different technologies. Some of my customers use Google Analytics, others use AWStats, and some use both. Which is better is often debated, but few people really understand the differences. Time to shed some light on the magic of web statistics.

This week one of my clients was hacked and asked me for emergency assistance to help secure their server infrastructure. It was a web server that ran WordPress websites on Apache (with PHP/MySQL), including a few webshops with customer data. This hack could easily have been prevented with the following best practices, is your server secure?

Few years ago my brother threw a beer on my iPhone in an Amsterdam bar. The poor thing didn't like the Dutch brew as much as I do: it died. While waiting for a new phone to arrive, I used an old one that couldn't do anything but texting, calling and... Snake! The idea for Snake '97 was born and this month it was time to update the wildly popular game.

At my home I have this crazy fast optical internet connection. It is a 600MB up and down fibre connection which directly arrives in my home (no copper cables involved). It's like a private internet highway. Reason enough to find out if I could do something to make better use of all this speedy fiber galore...

















