Remove unused network facing services from your website
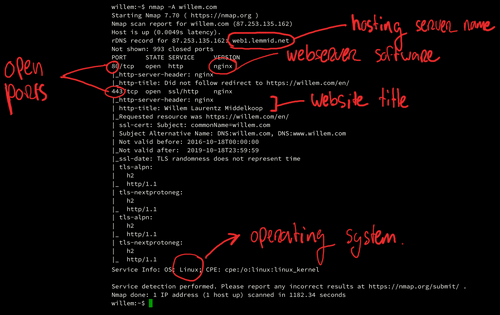
Considering open ports and unused network facing services
Feb. 28, 2019 - Willem L. Middelkoop
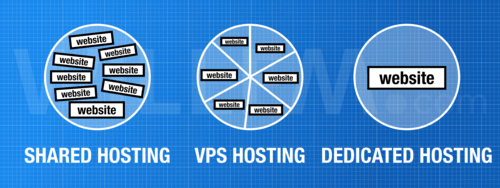
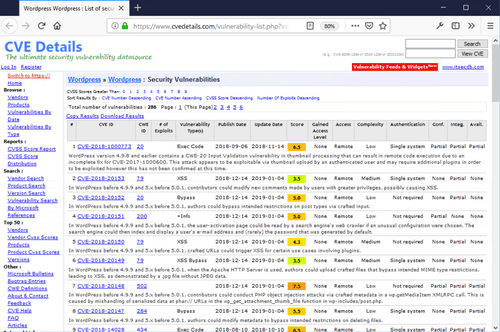
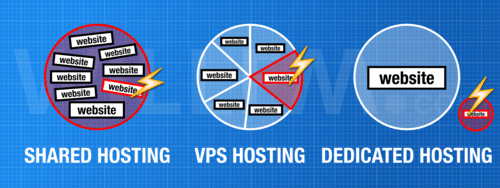
People pay me to hack them, provided I'll explain how it was done, so future hacks can be prevented. As security consultant, I scan for weaknesses in my clients' apps, webshops and websites. Very often a hack starts by exploiting a security hole that is visible remotely. Read along to learn how hackers find security holes and what you can do to secure them.
Continue reading