How to break net neutrality
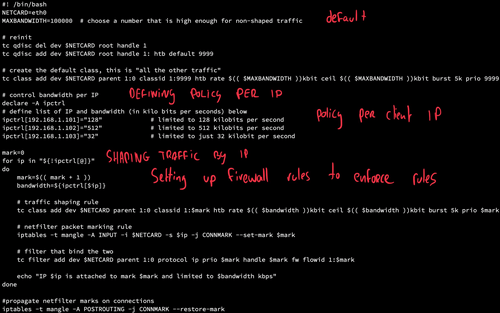
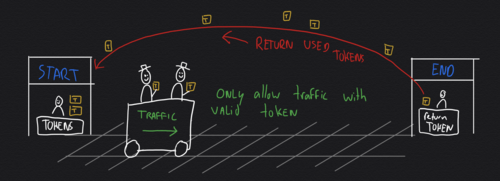
Limiting outbound network bandwidth per client IP-address
Apr. 1, 2020 - Willem L. Middelkoop
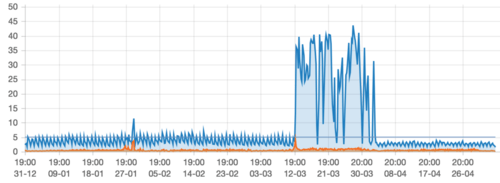
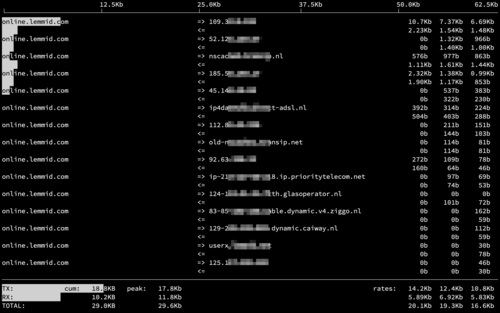
Last month I received an automated alert indicating excessive bandwidth usage, usually a sign of trouble. When this happens, you should follow a standard incident procedure, trying to isolate the source of the traffic before shutting it down. The cause of this incident was not what I expected however... requiring a different kind of mitigation than a simple blockade.
Continue reading